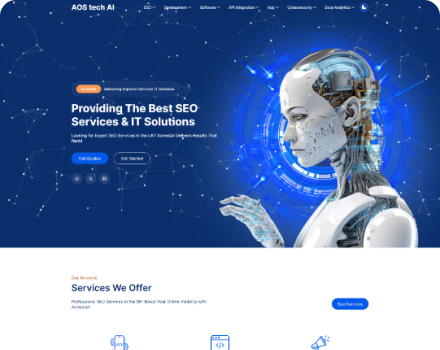
Eliminate costly API failures and integration breakdowns that disrupt your business operations. Our comprehensive API testing services identify critical vulnerabilities, performance bottlenecks, and security gaps.

Threat detection accuracy
Average emergency response time
Continuous monitoring subscription
UK businesses trust our cybersecurity expertise
Average cost savings per client

Our certified security experts conduct thorough website security audits to identify potential weaknesses in your digital infrastructure. We examine your code, server configurations, database security, and third-party integrations to create a comprehensive security baseline. This detailed assessment covers everything from SQL injection vulnerabilities to cross-site scripting threats, ensuring no security gap goes undetected. Our audit reports include prioritized recommendations and actionable insights to strengthen your overall security posture.
Advanced malware scanning technology continuously monitors your website for malicious code, infected files, and suspicious activities that could compromise your business operations. Our automated systems detect even the most sophisticated malware variants, including zero-day threats and polymorphic viruses that traditional scanners miss. When threats are identified, our expert team immediately initiates removal protocols while preserving your legitimate data and functionality. This service includes post-removal hardening to prevent reinfection.


Our state-of-the-art Security Operations Center provides round-the-clock monitoring of your digital assets using advanced threat intelligence feeds and behavioral analysis. We track emerging threats, monitor dark web activities related to your business, and analyze global cyber attack patterns to predict potential threats before they reach your systems. This proactive approach ensures your security measures evolve with the changing threat landscape, keeping you ahead of cybercriminals.
Comprehensive penetration testing conducted by certified ethical hackers simulates real-world cyber attacks to identify vulnerabilities that automated tools might miss. Our pen testing services include network security testing, web application security assessment, social engineering tests, and wireless network security evaluation. Each test follows industry-standard methodologies and provides detailed reports with practical remediation strategies. Regular pen testing ensures your security measures remain effective against evolving attack techniques.


Rapid response protocols ensure immediate action during security incidents, minimizing damage and reducing recovery time when breaches occur. Our incident response team follows established procedures to contain threats, preserve evidence, and restore normal operations quickly. We provide detailed incident analysis, regulatory compliance support, and post-incident security improvements to prevent similar attacks. This service includes business continuity planning to ensure minimal operational disruption during security events.






We begin every engagement with a thorough evaluation of your current security posture, examining all digital assets, infrastructure components, and potential attack vectors. Our certified security analysts conduct detailed vulnerability assessments, review existing security measures, and identify critical gaps that require immediate attention. This initial phase includes stakeholder interviews, technical documentation review, and baseline security testing to understand your unique risk profile. We also analyze your business requirements, compliance obligations, and budget considerations to develop a tailored security strategy that aligns with your organizational goals.

Based on our assessment findings, we design a comprehensive security monitoring strategy specifically tailored to your business needs and threat profile. This customized plan defines monitoring scope, detection rules, response protocols, and escalation procedures that align with your operational requirements. We establish security baselines, configure advanced monitoring tools, and create detailed incident response playbooks. Our planning phase also includes staff training recommendations, security awareness programs, and ongoing maintenance schedules to ensure long-term effectiveness.

Our technical team deploys state-of-the-art security monitoring infrastructure designed to provide comprehensive coverage of your digital environment. We implement advanced SIEM solutions, configure intelligent threat detection systems, and establish secure communication channels for real-time alerts and reporting. This phase includes integration with existing security tools, configuration of automated response mechanisms, and establishment of secure monitoring dashboards. We ensure minimal disruption to your operations while maximizing security coverage and detection capabilities.

Once deployed, our Security Operations Center provides 24/7 monitoring using advanced artificial intelligence and human expertise to detect and respond to security threats in real-time. Our security analysts continuously monitor your environment, analyze threat intelligence feeds, and conduct proactive threat hunting activities to identify advanced persistent threats. We maintain detailed logs of all security events, provide regular status reports, and continuously fine-tune detection rules based on emerging threats. This ongoing monitoring includes regular security health checks and performance optimization.

When security incidents occur, our expert response team immediately implements containment measures, conducts thorough forensic analysis, and coordinates recovery efforts to restore normal operations quickly. We provide detailed incident reports, regulatory compliance support, and recommendations for preventing similar future incidents. Our continuous improvement process includes regular strategy reviews, security technology updates, and adaptation to emerging threats. We also provide ongoing security consultations, staff training updates, and strategic planning support to ensure your security posture evolves in line with your business needs.When security incidents occur, our expert response team immediately implements containment measures, conducts thorough forensic analysis, and coordinates recovery efforts to restore normal operations quickly. We provide detailed incident reports, regulatory compliance support, and recommendations for preventing similar future incidents. Our continuous improvement process includes regular strategy reviews, security technology updates, and adaptation to emerging threats. We also provide ongoing security consultations, staff training updates, and strategic planning support to ensure your security posture evolves in line with your business needs.
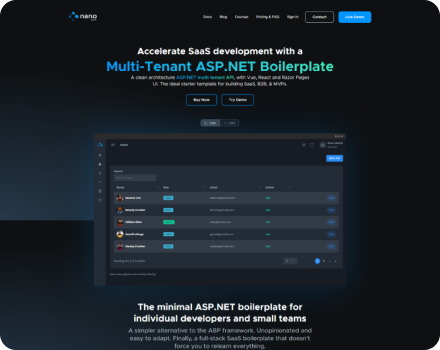
Start with what you need, customize as you go.